OSI LAYER MODEL BASED ON SCENARIO
OSI Layer Model For Student :
This OSI Layer Model discussion will begin with a Cobham Collage Campus network connecting to their private network's Online Learning System Server via their home network (public IP address) (Private IP Address). Assume that the Cobham College Campus network is attempting to upload a file to the Cobham College Online Learning System.
Let's start with the Application Layer, where data transit services such as SMTP, POP3, and others are supplied to the file that a Cobham Collage student wishes to submit into the Cobham Collage Online Learning System platform. The data is transported using the file transfer protocol (FTP) in this situation.
On the Presentation Layer, the file will be converted to binary format, and file compression will begin in order to reduce the file's size. A 7MB file, will be compressed down to 3MB, allowing the content to be transferred even faster. Finally, it will encrypt the file delivered by the sender using SSL or another security protocol for data security concerns.
The data will subsequently be transmitted to the Session Layer, which will manage the communication session without interfering with the communicating systems' ability to communicate. The packet data unit for these three processes is data, which will be broken down into segments in the next phase.
This Transit layer is where the segmentation begins. Each segment contains the source and destination port numbers, as well as the sequence number. The port number's purpose is to get the data on the appropriate track, whereas the sequence number's goal is to reorder the out-of-order segments. Furthermore, error control is an important part of this layer since it determines whether the segments have arrived and, if not, re-sends them. The two protocols employed in this operation are TCP and UDP. In our instance, TCP will be used to send the file since it assures that each data packet is transmitted and receives a message indicating whether or not the data has been received. Why didn't we utilise UDP instead of TCP? Because UDP is primarily used for video streaming, it does not reply to whether or not the data has been reached.
The Network layer is the following layer, and it's here that the crucial parts of our data trip are influenced by the scenario due to communication between public and private IP addresses. This layer is responsible for delivering packets (PDU) from the original source (Sender) to the final destination (Receiver). Logical addressing, which allocates an IPv4 destination to each segment, and routing, which handles packet delivery based on the IP address and subnet mask, are two procedures involved in this layer. Because of the public to private IP address, the routing will be different in this situation, with the sender (Public IP address) transmitting the data to the Cobham Collage Campus network main router (Public IP address), and then another routing within the Cobham Collage Private IP Address to transfer the data to the requested host.
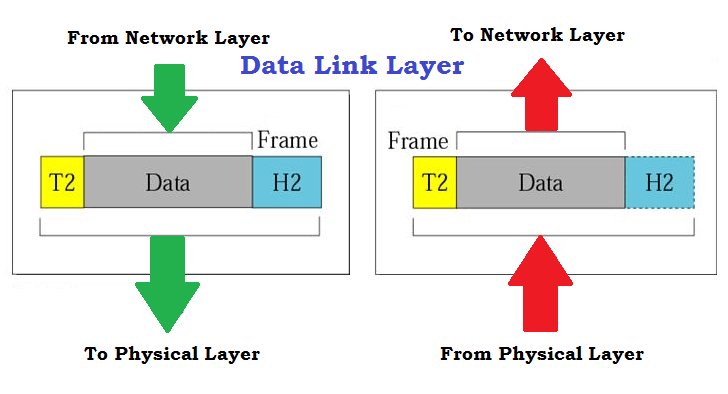
The Data Link layer is the next layer, where the hardware's MAC address is appended to the packet and the frame is created. The objective of MAC is to maintain track of data packets as they go over a shared channel from one Network Interface Card (NIC) to another (Hop-to-Hop Delivery).
Finally, the Physical Layer is in charge of moving bits from one layer to the next. In addition, the physical layer converts binary into a signal that can be transmitted over a medium. In this scenario, wireless and wired media are used.
Hop-hop delivery now takes place from the modem at the home of Cobham College students to the main network of the Cobham College campus. If the target source is legitimate, this method will only work from grades 1 to 3, and then to grades 4 to 7. To decrypt a file that a Cobham University student downloaded, we'll start with the Physical layer and continue on to the Application layer. First, on the Physical layer, where data is received over wired media, before moving on to the next layer.
Second, the source and destination MAC addresses are removed at the Data link layer, converting the frame to a packet and the logical address will be erased if a valid destination is found at the Network layer (packet to segments). Hop-to-hop delivery to the next node is used if the destination is invalid. Data (segment) will check sequence addressing to see whether data has been misplaced during transmission, and port addressing will use error control techniques to verify whether the destination has been reached on the Transport layer. The Session ends at this layer, and no further communication between the two participants will be possible; if more communication is desired, another request to start a new dialogue session must be sent.
While being at the Presentation layer, the data will be converted back to its original form, and it will be decrypted using the same encryption process used on the transmitting side. Finally, the permission to read, write, and view the file sent over the public network by a Cobham College student will be provided by Application layer .
1. Physical Layer
2. Data Link Layer
3. Network Layer
4. Transport Layer
5. Session Layer
6.Presentation Layer
7. Application Layer
Network Component For Data Communication
In order for the students to access the Online Learning System located in the Cobham College network facilities, network component is needed to connect student to the public network to connect the Cobham College facilities. Computer networks components comprise both physical parts as well as the software required for installing computer networks, both at organizations and at home. The hardware components are the server, client, peer, transmission medium, and connecting devices. The software components are operating system and protocols.
1. Message:
The message is the information (data) to be communicated. Common forms of information include text, numbers, pictures, audio, and video.
2. Sender:
The sender is the device that sends the data message. It can be a computer, workstation, telephone handset, and video camera
3. Receiver:
The receiver is the device that receives the message. It can be a computer, workstation, telephone handset, and television
4. Transmission medium:
The transmission medium is the physical path by which a message travels from sender to receiver. Some examples of transmission media include twisted-pair wire, coaxial cable, fiber-optic cable, and radio waves.
5. Protocol:
A protocol is a set of rules that govern data communications. It represents an agreement between the communicating devices. Without a protocol, two devices may be connected but not communicating, just as a person speaking French cannot be understood by a person who speaks only Japanese.

.png)